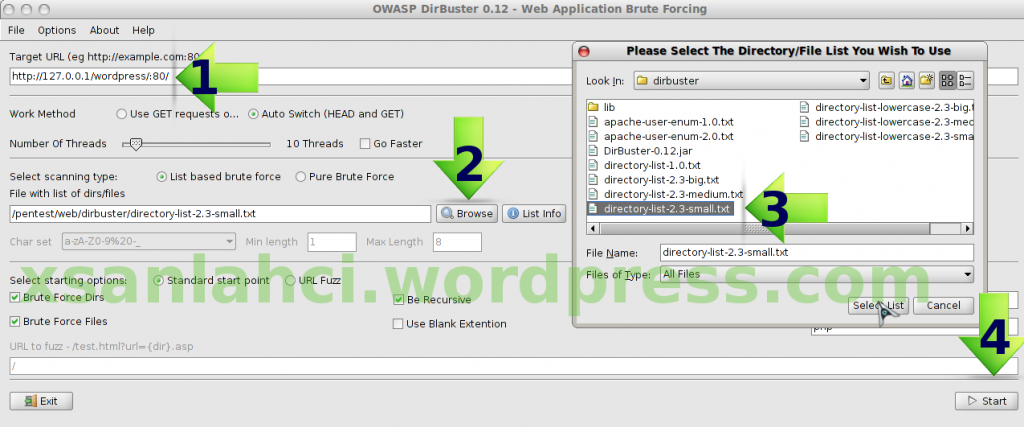
Digital forensics is the science of analyzing digital evidence. Digital evidence is extracted from the electronic evidence such as Personal Computers, mobilephone, notebook, server, any technological tool that has the storage media and can be analyzed.
(Digital forensik adalah ilmu yang menganalisa barang bukti digital. Barang bukti digital merupakan hasil ekstrak dari barang bukti elektronik seperti Personal Komputer, mobilephone, notebook, server, alat teknologi apapun yang mempunyai media penyimpanan dan bisa dianalisa.)
Steps of digital forensic
1. Identification
means that we chose the thing will identificate with forensic. Example : PC, mobilephone, notebook, flasdisck, server.
2. Preservation
-chain of custody (to ensure that file when it last changed the owner)
-labeling
-imaging/clone
3. Examination
4. Analysis
5. Reporting/produck
The first step is check the position of flasdisk. The goal is to ensure that the data which we will identification. do not let any of the data format the pc itself. If Flasdisck previously been formatted with verascrypt it must be in the format.
1. To find the position of flasdisk which will we identification, open terminal
#fdisk -l or dmesg enter
2. To reformat the flasdisk from verascypt position to normal position
#cfdisk /dev/sdb1enter
-delete
-new
-primary
-write
-type : yes
-quite
#mkfs.fat /dev/sdb1 enter
from command the flasdisk has reformated.
3. Let start to identification the forensic of flasdisk
to know what data has been erased and can be read back. (manual ways)
#fdisk -l
#testdisk /dev/sdb
-process
-intel
-analisis
-quick search
-continue
-pilih P: list file
red colour :
Data that has been erased before and will be in recovery
white colour : Data is still stored in flasdisk
to check the file has recovered search in root/home directory
4.
The next way is an automatic recovery.
#fdisk -l
#photorec /dev/sdb enter
- enter
previous data will be erased recovery back and immediately stored in a single folder in the home directory namely recup_dir